OpenLDAP Guide
提示
Enterprise EditionQuick Overview
提示
Docker Compose Configuration File
version: '1'
networks:
go-ldap-admin:
driver: bridge
services:
openldap:
image: osixia/openldap:1.5.0
container_name: go-ldap-admin-openldap
hostname: go-ldap-admin-openldap
restart: always
environment:
TZ: Asia/Shanghai
LDAP_ORGANISATION: "flashduty.com"
LDAP_DOMAIN: "flashduty.com"
LDAP_ADMIN_PASSWORD: "password"
volumes:
- ./openldap/ldap/database:/var/lib/ldap
- ./openldap/ldap/config:/etc/ldap/slapd.d
ports:
- 389:389
networks:
- go-ldap-admin
phpldapadmin:
image: osixia/phpldapadmin:0.9.0
container_name: go-ldap-admin-phpldapadmin
hostname: go-ldap-admin-phpldapadmin
restart: always
environment:
TZ: Asia/Shanghai
PHPLDAPADMIN_HTTPS: "false"
PHPLDAPADMIN_LDAP_HOSTS: go-ldap-admin-openldap
ports:
- 8088:80
volumes:
- ./openldap/phpadmin:/var/www/phpldapadmin
depends_on:
- openldap
links:
- openldap:go-ldap-admin-openldap
networks:
- go-ldap-admin
提示
Starting the Service
docker-compose updocker-compose up -dUse the following command to check the service status:
docker-compose psWhen you want to stop the service, use:
docker-compose downLogging into OpenLDAP
OpenLDAP Configuration
Adding Groups and Users
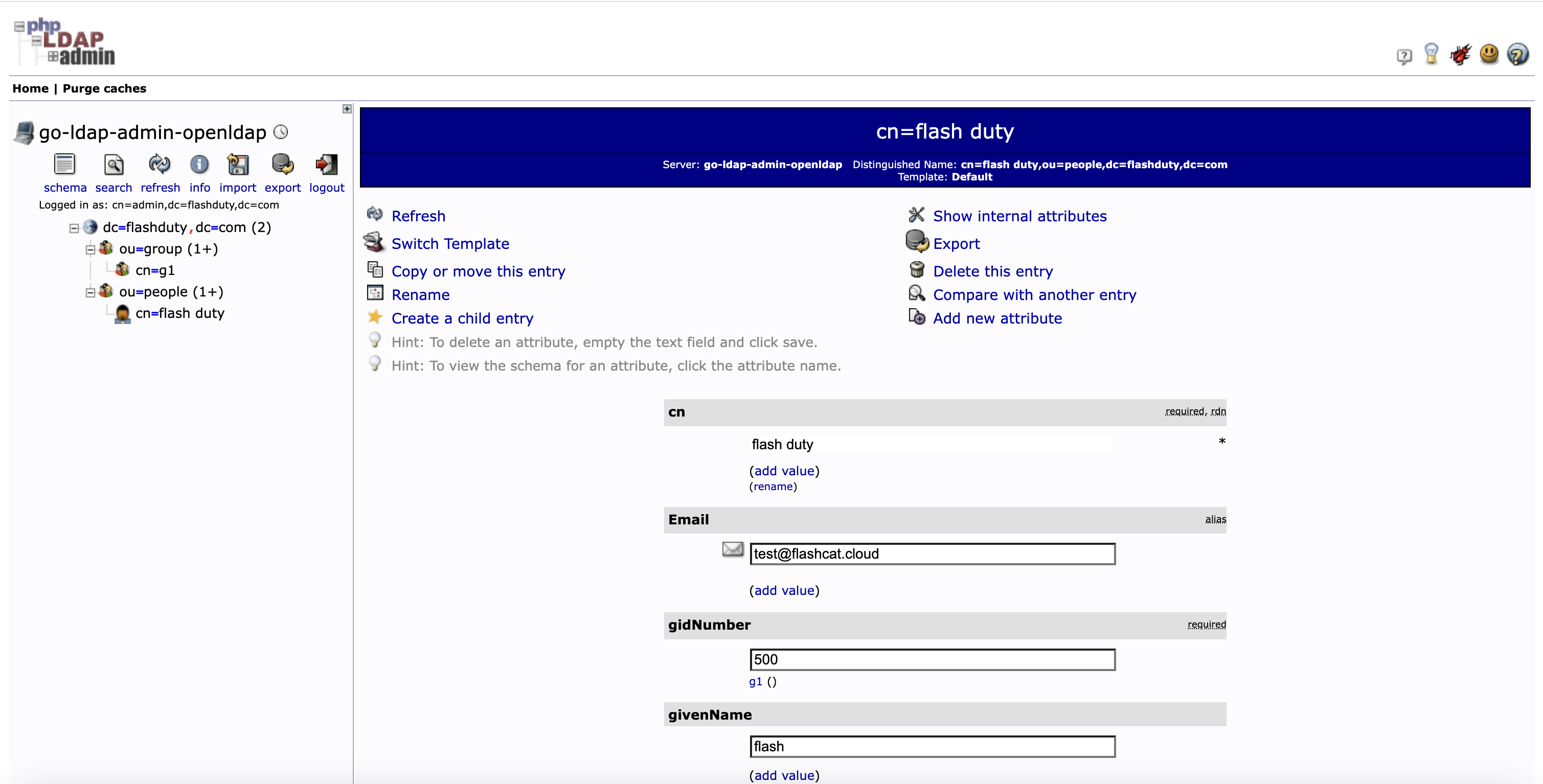
提示
User Path (e.g., cn=flash duty under ou=people in the above image) -> Add new attribute -> select Email to add the Email attribute for the user. Ignore if it already exists.FlashDuty Integration
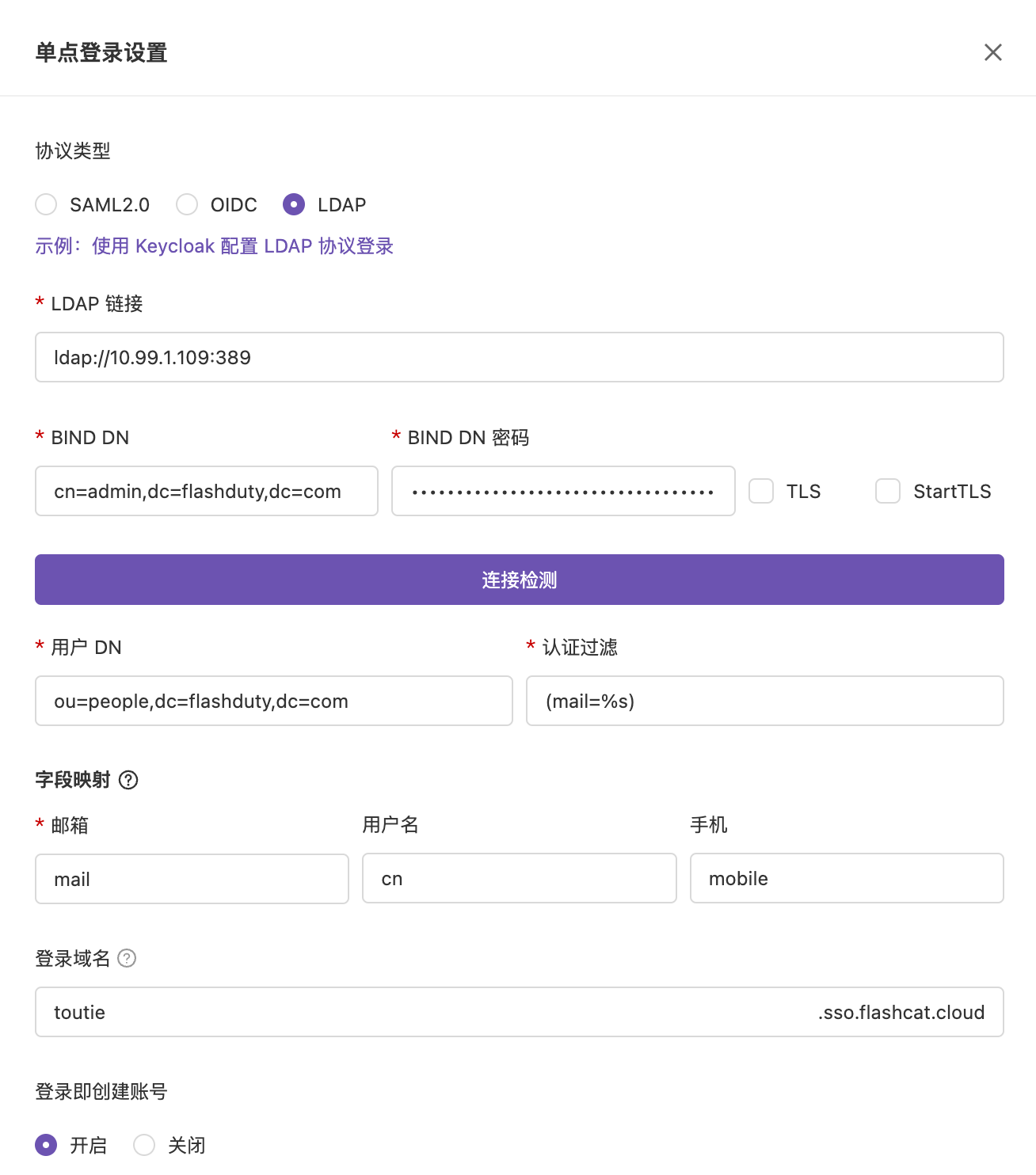
提示
修改于 2024-11-25 03:15:57



